Configure OpenShift Authentication
RHODS itself has no particular authentication settings.
Instead, it relies on how OpenShift’s authentication has been configured.
Therefore, it’s important to have at least one Identity Provider configured.
The steps below will walk you through 2 fairly simple Identity Providers to get you started.
Log in to console.redhat.com
Make sure you are logged in https://console.redhat.com/.
If not already done, go to https://console.redhat.com/ and log in with your Red Hat account. Once you are logged in, navigate to the OpenShift Section. (https://console.redhat.com/openshift). You should see your cluster(s).
Display detailed instructions:
Configure HTPasswd as an Identity Provider
This is a good option to use if you only need a single user and/or if you want to start by creating a Cluster Administrator account.
That is how we will set it up:
Add the Identity Provider
-
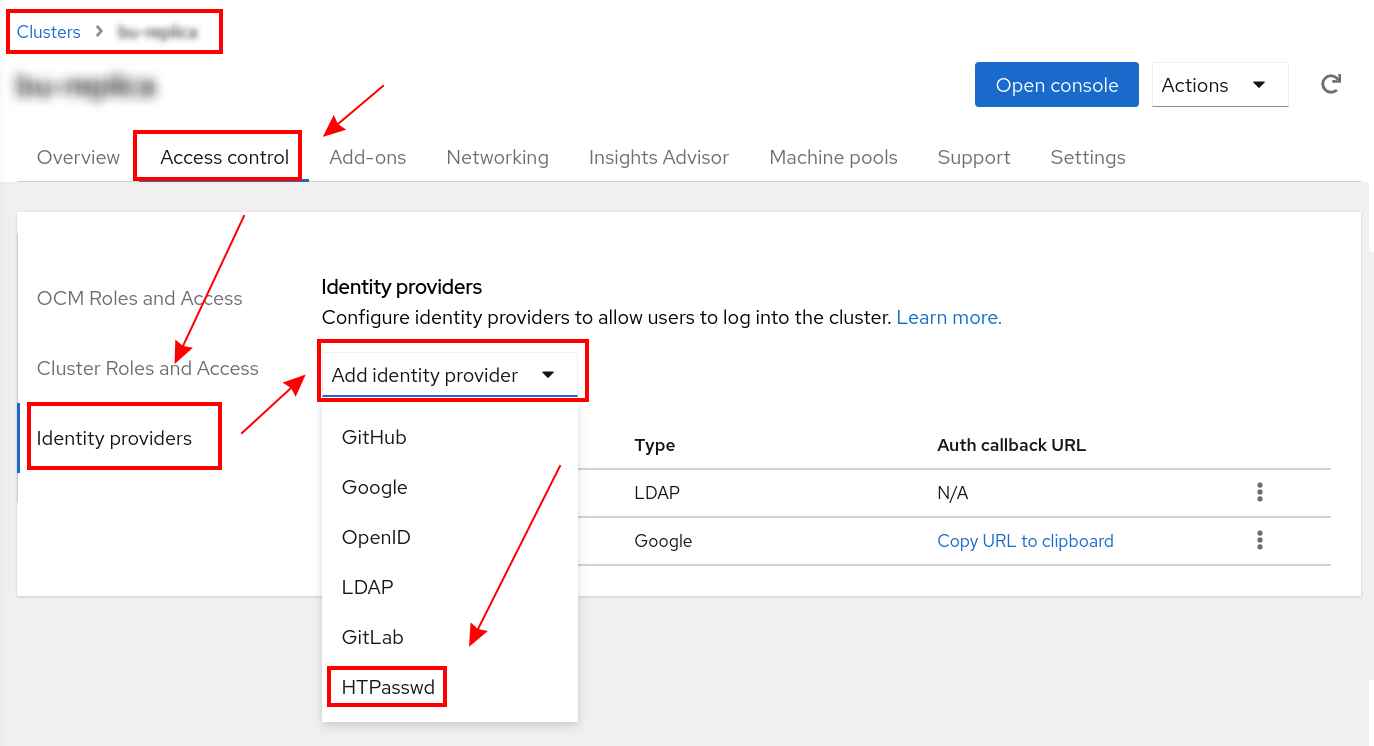
Choose the Access control tab for your cluster
-
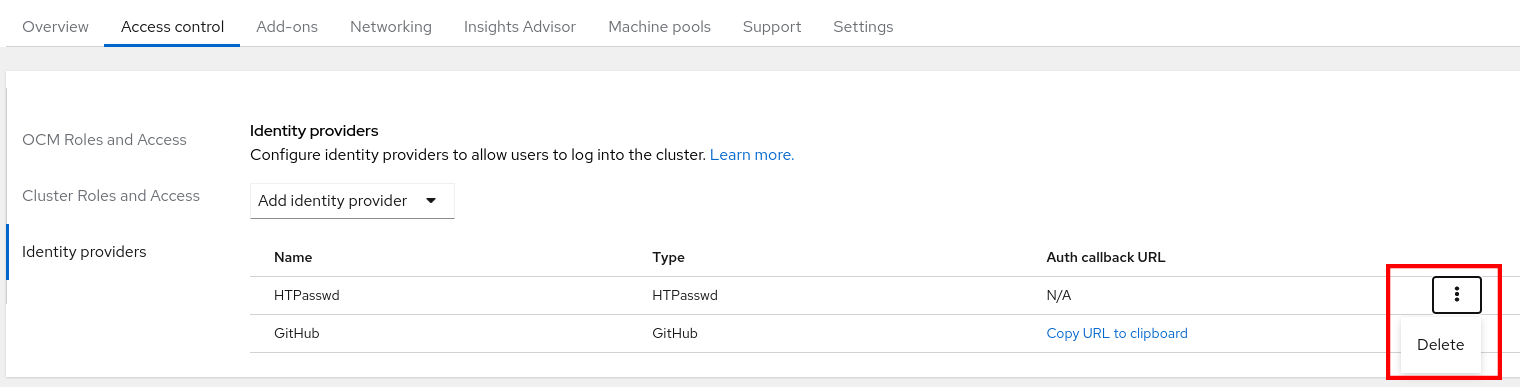
Select Identity providers
-
Click the Dropdown to Add identity provider and choose HTPasswd
-
On the next screen, keep all the defaults, including the suggested username and password
-
Make sure to save them somewhere
They will not be shown again.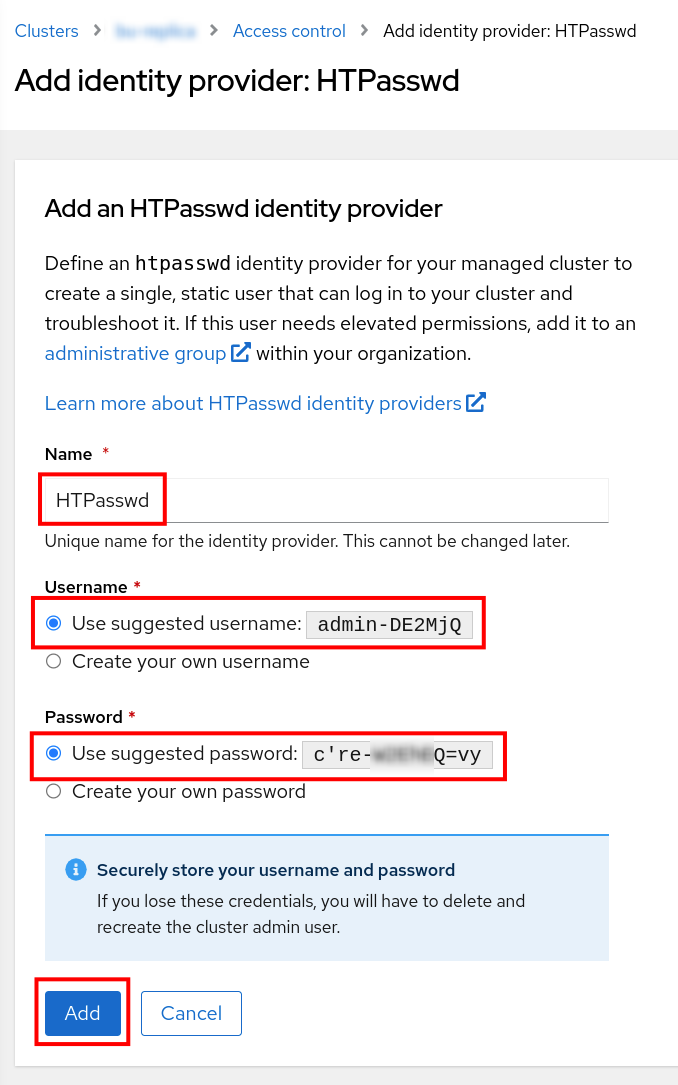
-
click Add
Make this new user a Cluster-Admin
-
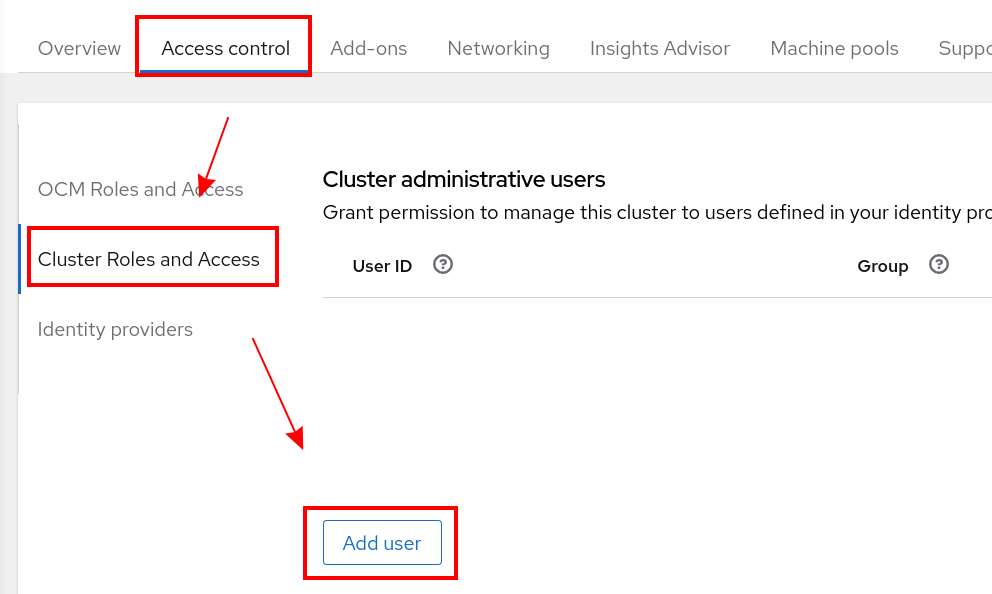
Select Cluster Roles and Access
-
Click Add User
-
Enter the name of the
admin-account that was created in the previous step, and choose Cluster-Admins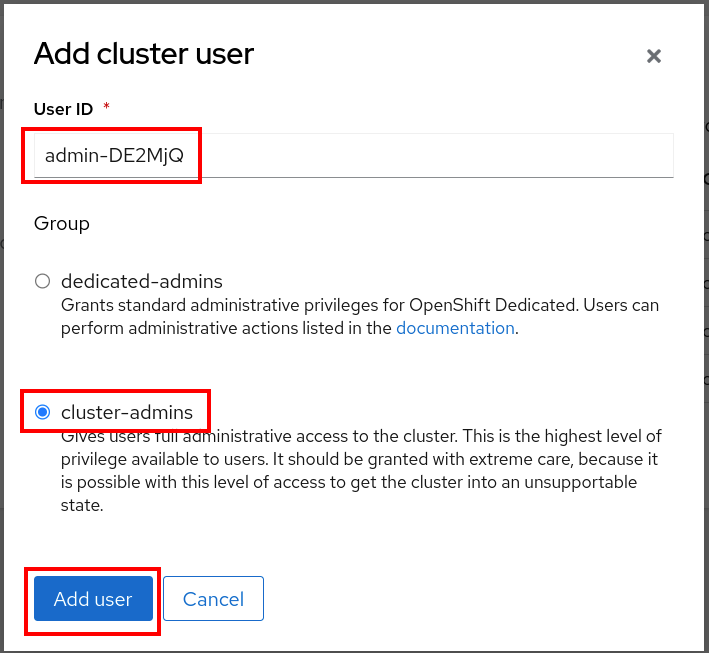
-
Click Add User
-
Confirm you can log into OpenShift
-
To confirm, click on the blue button (Open Console).
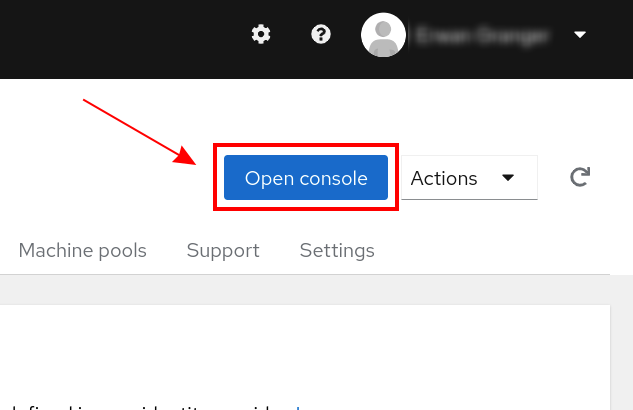
-
A new tab will open, prompting you to choose an Identity Provider+ choose HTPasswd, the one we just added
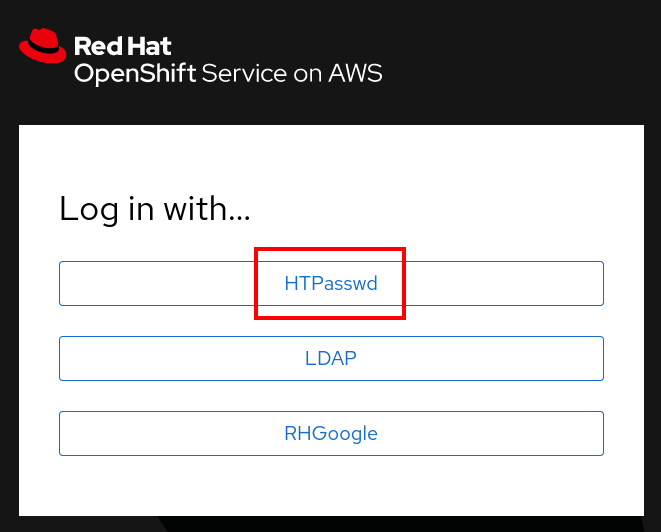
-
On the next screen, enter the credentials that we were generated for you.
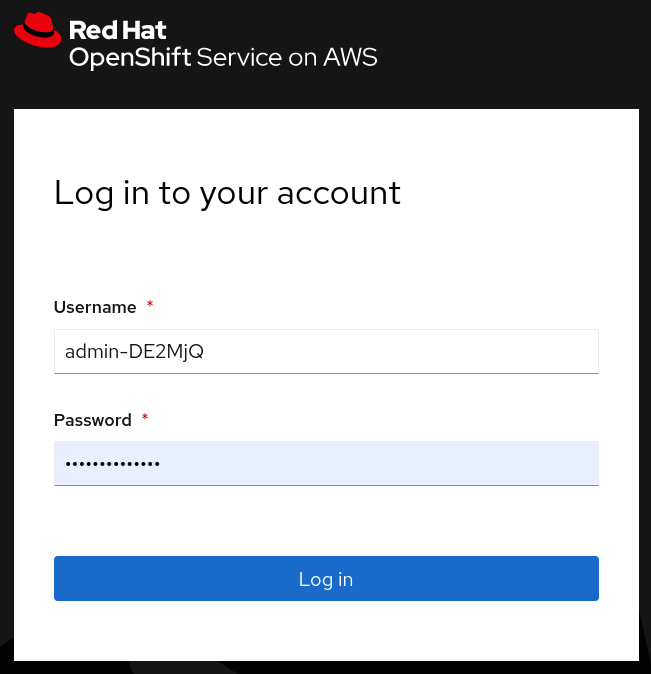
-
You should now be logged into the OpenShift Console
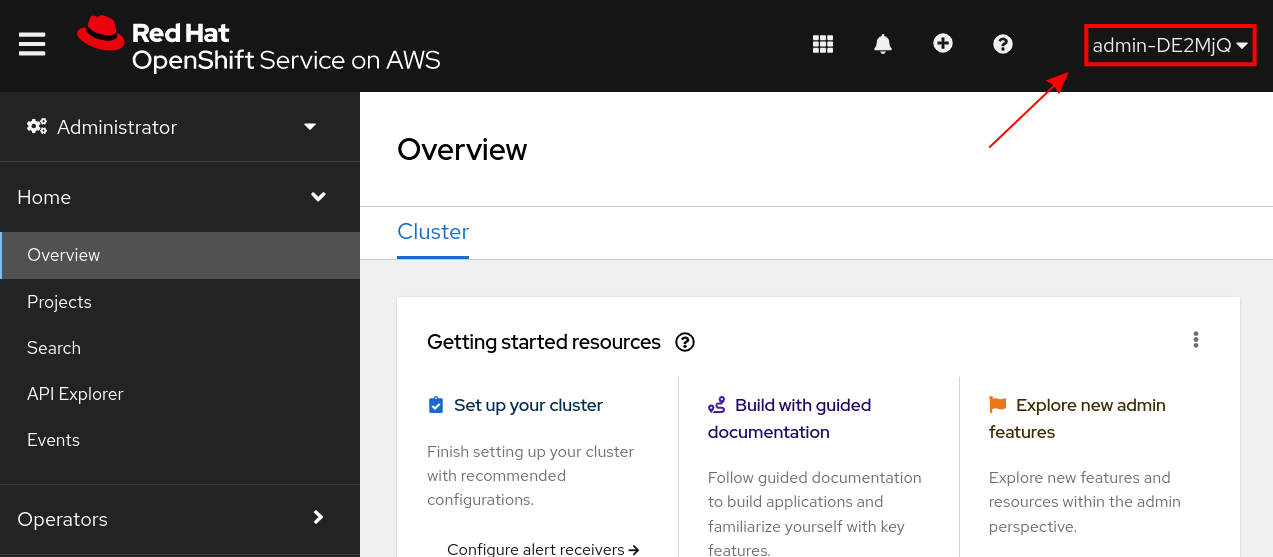
-
If your screen looks like the above, kudos, you’ve just created an admin account for your OpenShift cluster
The next section will show you how to use Github Authentication in order to easily grant access to many users.
Configure GitHub as an Identity provider for additional users
One of the fastest ways to grant access to many users is to add a GitHub Identity Provider to your OpenShift Cluster.
This only requires you (and them) to have a GitHub account.
If you’ve never done it before, the instructions below will guide you.
Create a GitHub Organization
-
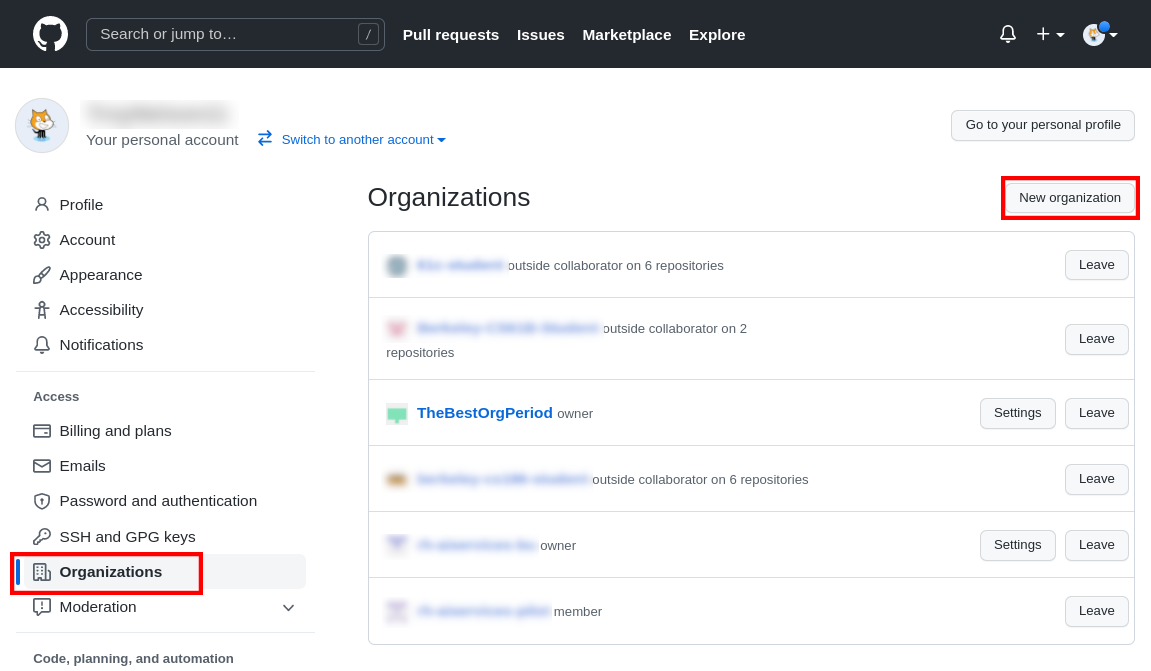
Log into GitHub and go to the Organizations page
-
Create a new Org. (Must be an “Owner”)
-
Organizations → New Organization
-
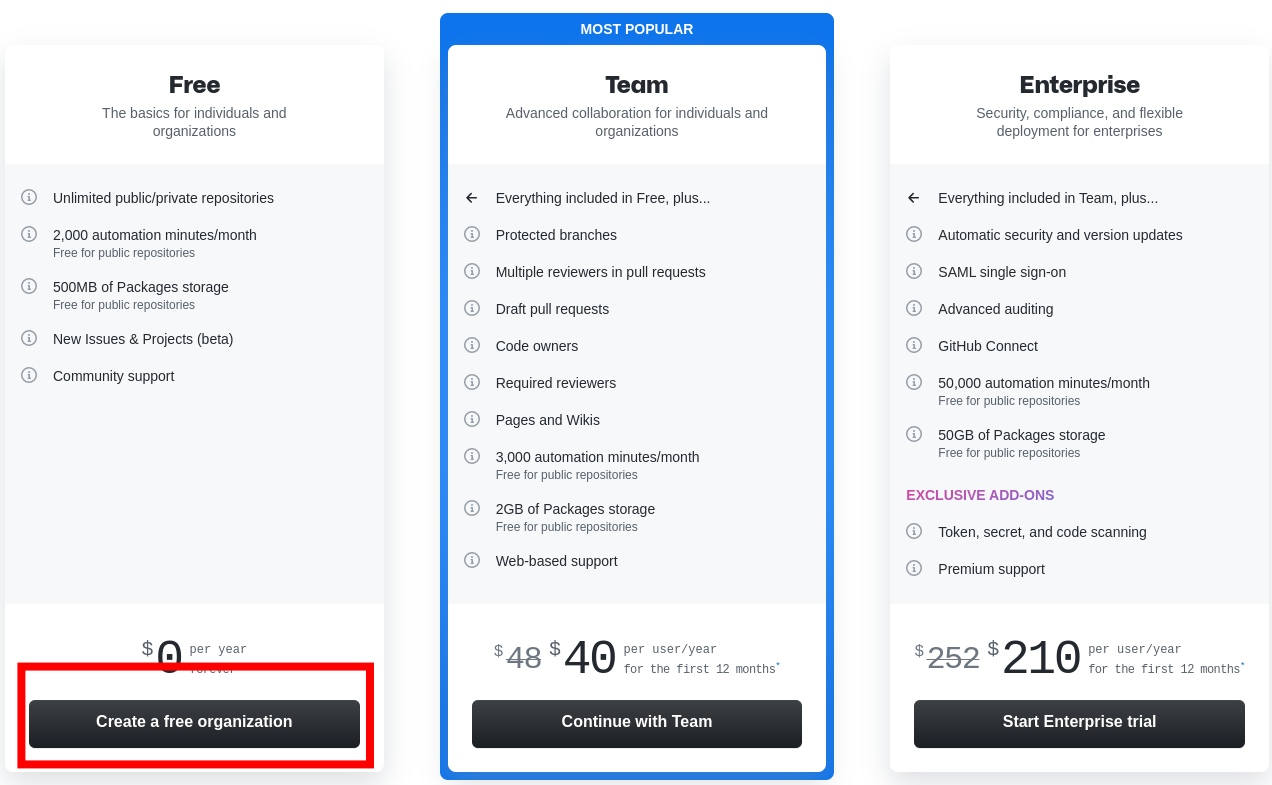
Choose to create a free Organization
-
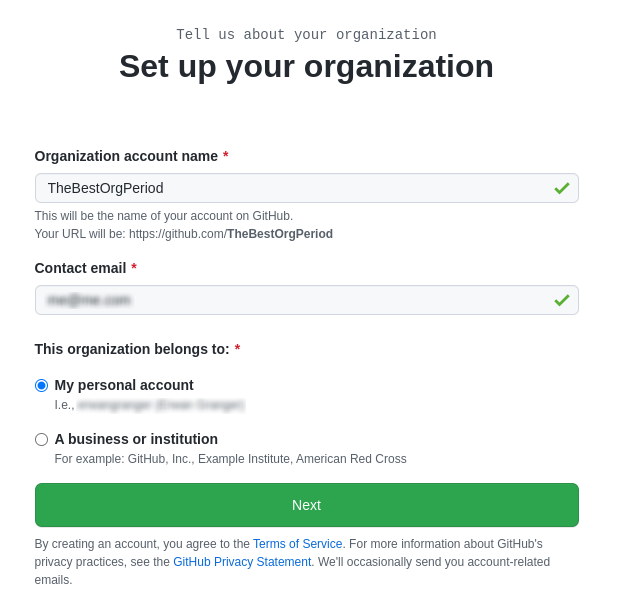
Fill out and indicate if creating an enterprise org
-
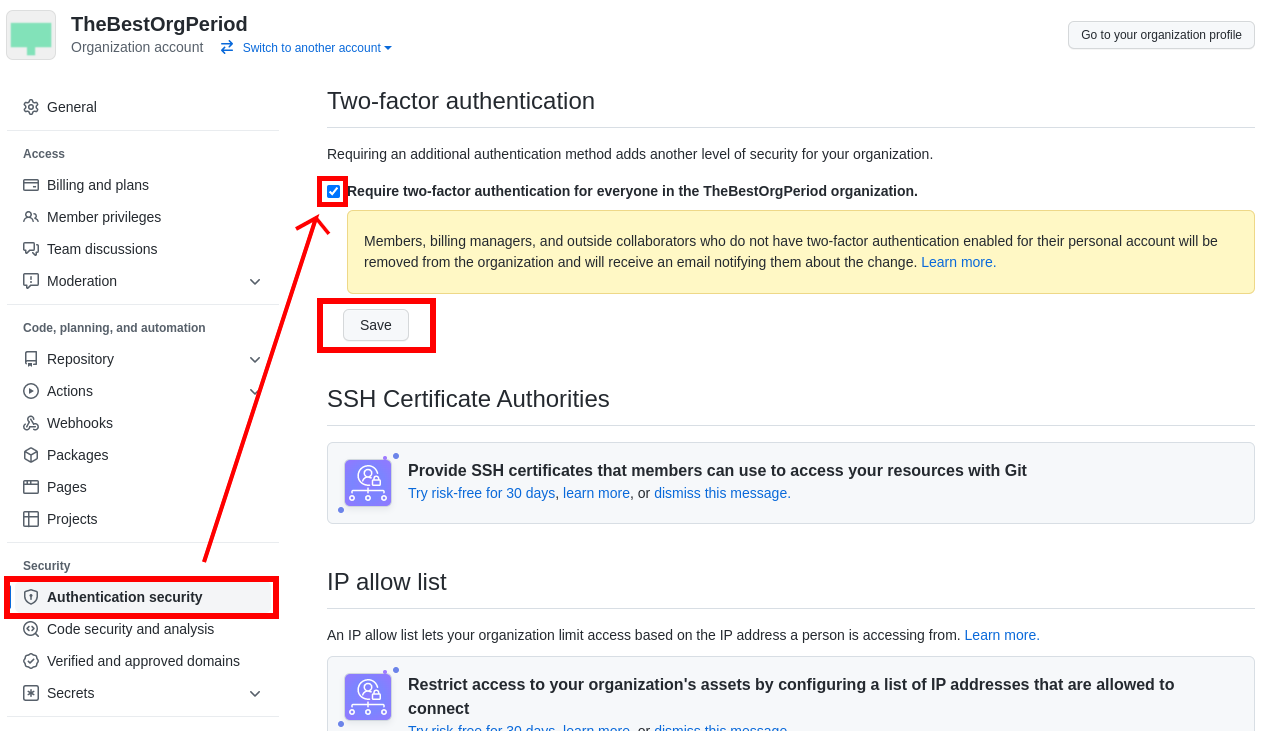
Enforce 2FA for the GitHub Organization - (Optional but recommended)
-
This setting requires invited users to activate another authentication method. This will add a layer of security to their Github login, and therefore to the access to OpenShift and RHODS.
Invite users to your organization
-
Your new Organization should now be ready
-
Invite additional users to the organization
Configure Github Identity provider in Red Hat Hybrid Cloud Console
-
The video below showcases the steps to be executed in order to configure the newly created Github Org as the authentication provider for the OpenShift Cluster.
The steps shown in the video are described below:
-
In the Red Hat Hybrid Cloud console (https://console.redhat.com)
-
Select your cluster
-
Copy the link from Open console Button into the Homepage URL on Github
-
-
In Github (https://github.com/)
-
Select your Github organization and go to Settings
-
Go to Developer settings (bottom)
-
Select OAuth Apps
-
Click New OAuth App
-
-
In the Register a new OAuth page:
-
Choose an Application Name
-
Paste the URL of your cluster as the Homepage URL
-
-
Back in the Red Hat Hybrid Cloud console (https://console.redhat.com)
-
Select your cluster
-
Go to the Access Control tab
-
Click on Add identity provider
-
Select Github in the dropdown list
-
Edit the Name to something meaningful, such as Github-Auth
-
Copy the Oauth Callback URL
-
Paste that URL into the Github screen asking you for it
-
Click on the Register Application button in the github screen
-
On the next screen, copy the Client ID from Github into the Red Hat Hybrid Console screen
-
Click on Generate a new client secret and also copy that secret into the Red Hat Hybrid Console screen
-
Finally, enter the Github Organization name into the Red Hat Hybrid Console and click *Add
-
Make yourself and other GitHub users cluster-admins (Must be in Org)
-
Choose the Access control tab for your cluster
-
Select Cluster Roles and Access
-
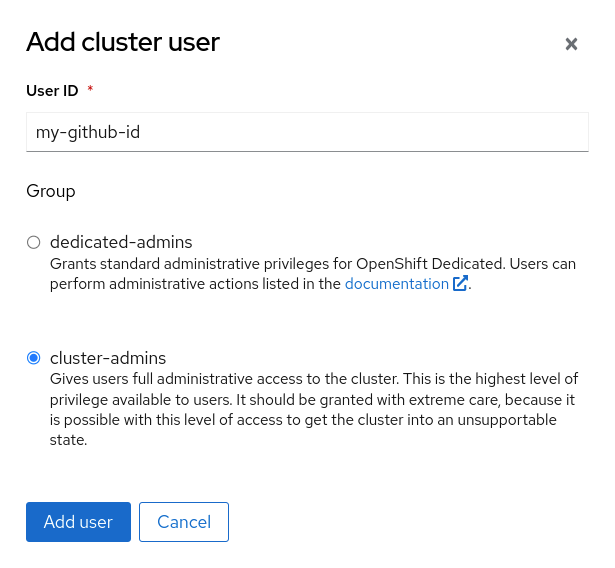
Add user (Provide Github Username)

-
Add your own Github ID as a Cluster-Admin
-
-
You should now be able to login using GitHub authentication
-
The first time you do so, you will be prompted to authorize the connection.